As a Software Tester, I spend a lot of time executing exploratory tests on websites. Recently I came across a simple method to incorporate Security Testing into an exploratory testing workflow. The bonuses of this method are:
- the security tool setup is quick
- no prior knowledge of security testing is required
- the security testing happens automatically in the background while you are performing your exploratory tests
The tools required for this are:
Owasp Zap is an open source Security Testing tool. This tool is used by experienced Security Testers and is packed with a range of useful tools. For this blog post, we’re going to use the simple, yet extremely useful, Passive Scanner. We will configure Zap to act as a proxy between a browser and server, permitting it to automatically scan the HTTP request and response messages generated during the testing.
Owasp Juice Shop is your own private, intentionally insecure web application which makes it great to practice Security Testing on without getting into trouble. This is an optional requirement - if you already have a local website running on your machine that you want to test on, then use that instead.
Preparation
To prepare Zap, perform the following three steps:
- Install Zap (requires Java).
- Configure your browser to use Zap as a proxy.
- Install the Zap root CA certificate into your browser’s list of trusted root certificates.
Test execution
- Open Zap - this will automatically launch the proxy server and the passive scanner.
- Open a browser.
- Navigate to the website you want to test.
- Start the execution of your tests.
- Some time later, stop the execution of your tests.
- Go to Zap and look in the Alerts tab.
Results
The Alerts tab will display all of the issues that the passive scanner detected while the tests were being executed.
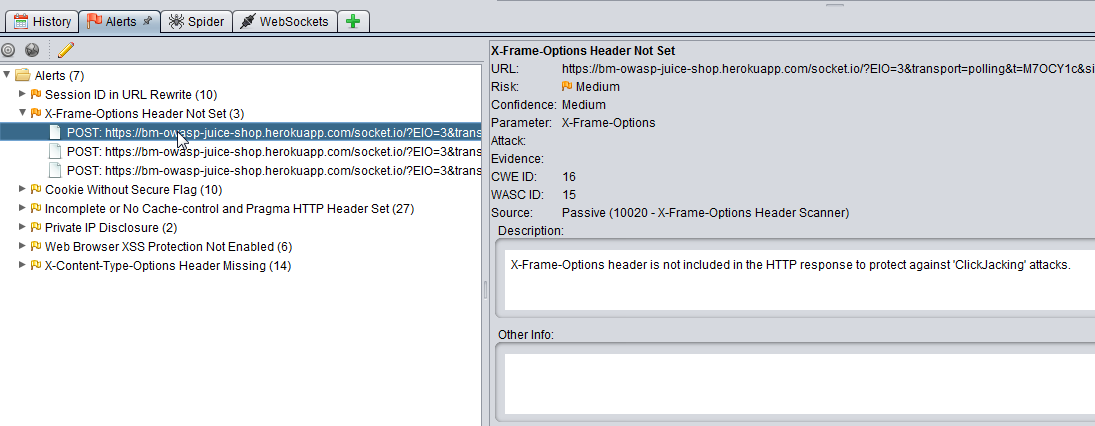
The alerts will be displayed in a tree structure grouped by Alert Type, and will show the number found along with the URL they occurred on. The types of alerts found will vary depending on the website but can include:
- X-Frame-Options Header Scanner
- Session ID in URL Rewrite
- Cookie Without Secure Flag
- Private IP Disclosure
You can click on these to get advice from Zap on how to address them, and then discuss your findings within your team.
Extend
There is a lot more you can do with the Passive Scanner:
- execute your automated UI tests through the passive scanner
- mobile website testing by proxying a device through your machine and Zap
- and many more
You can also explore the many other tools within Zap which we will do in future posts.
